Many organizations want to delegate enabling and disabling MFA for a user to their helpdesk, but the only RBAC role that allows MFA management is the Global Administrator and no one wants to grant helpdesk technicians Global Admin access to their tenant. However, there is a way around this RBAC limitation if your organization has Azure AD Premium.
General Concept
At a high level enabling and disabling MFA will be managed by adding and removing users from a security group. The security group will be included in a Conditional Access policy which defines the MFA requirements.
Setup
Requirements
- Admin with Conditional Access administrator role
- Helpdesk user(s) with User Administrator role assigned
Setup
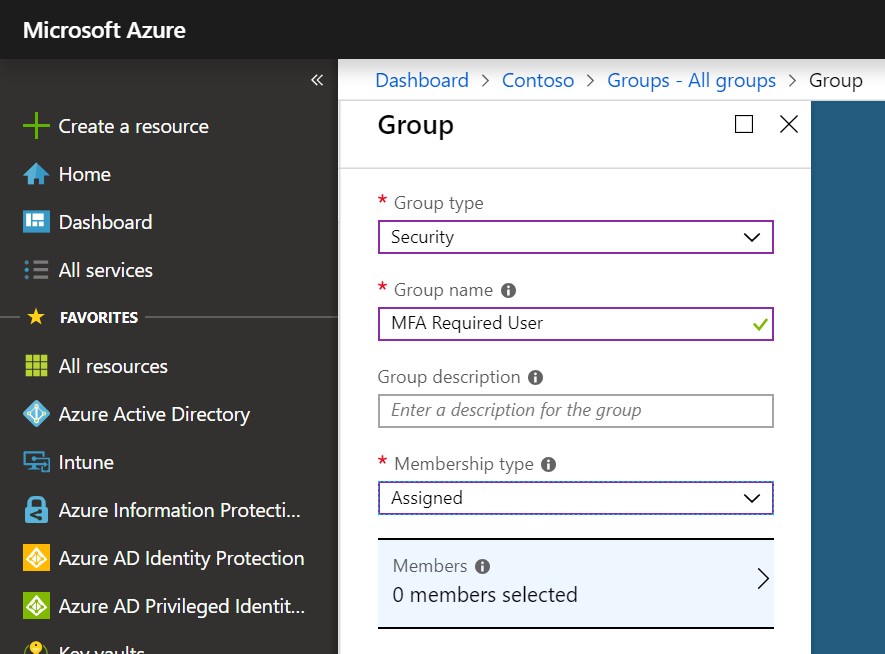
Have a Helpdesk user create a security group in Azure Active Directory and assign the users your organization wants to require MFA when accessing applications. Make sure to include a descriptive name like MFA Required Users.
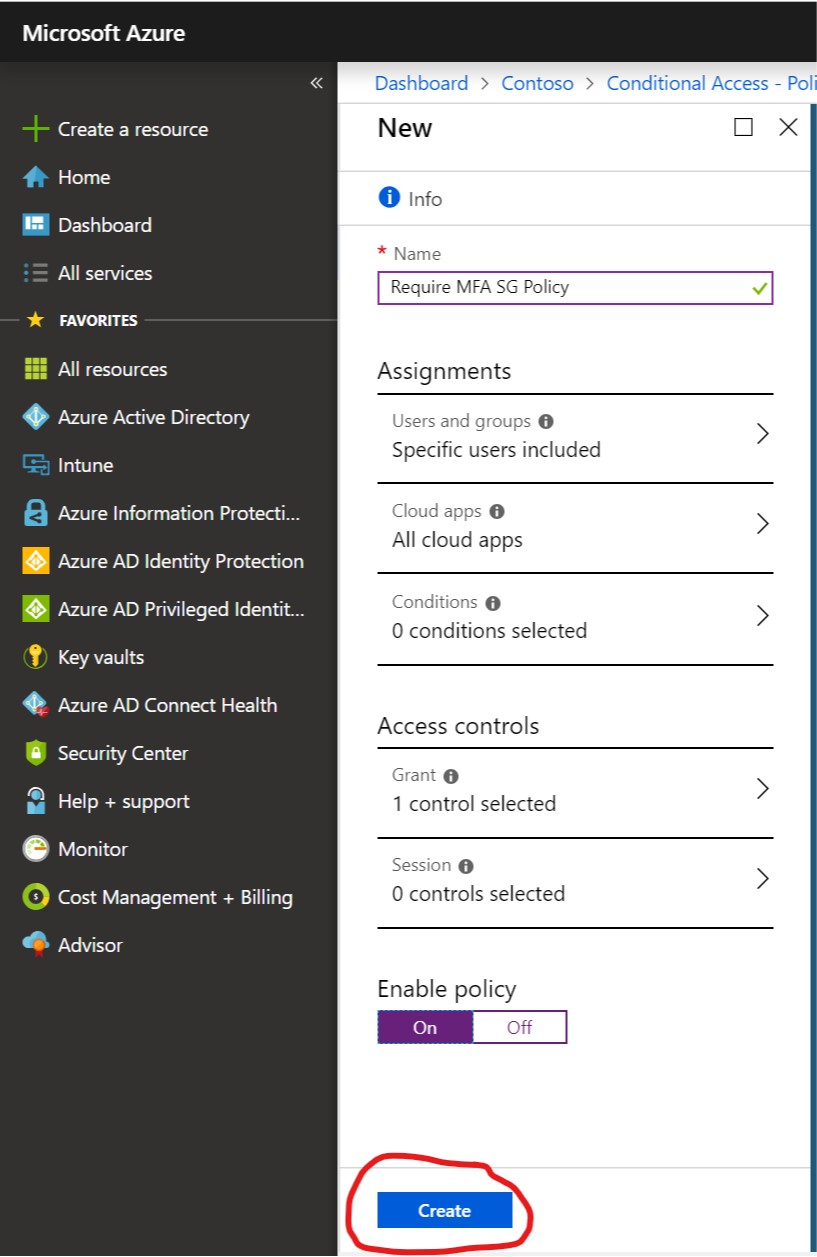
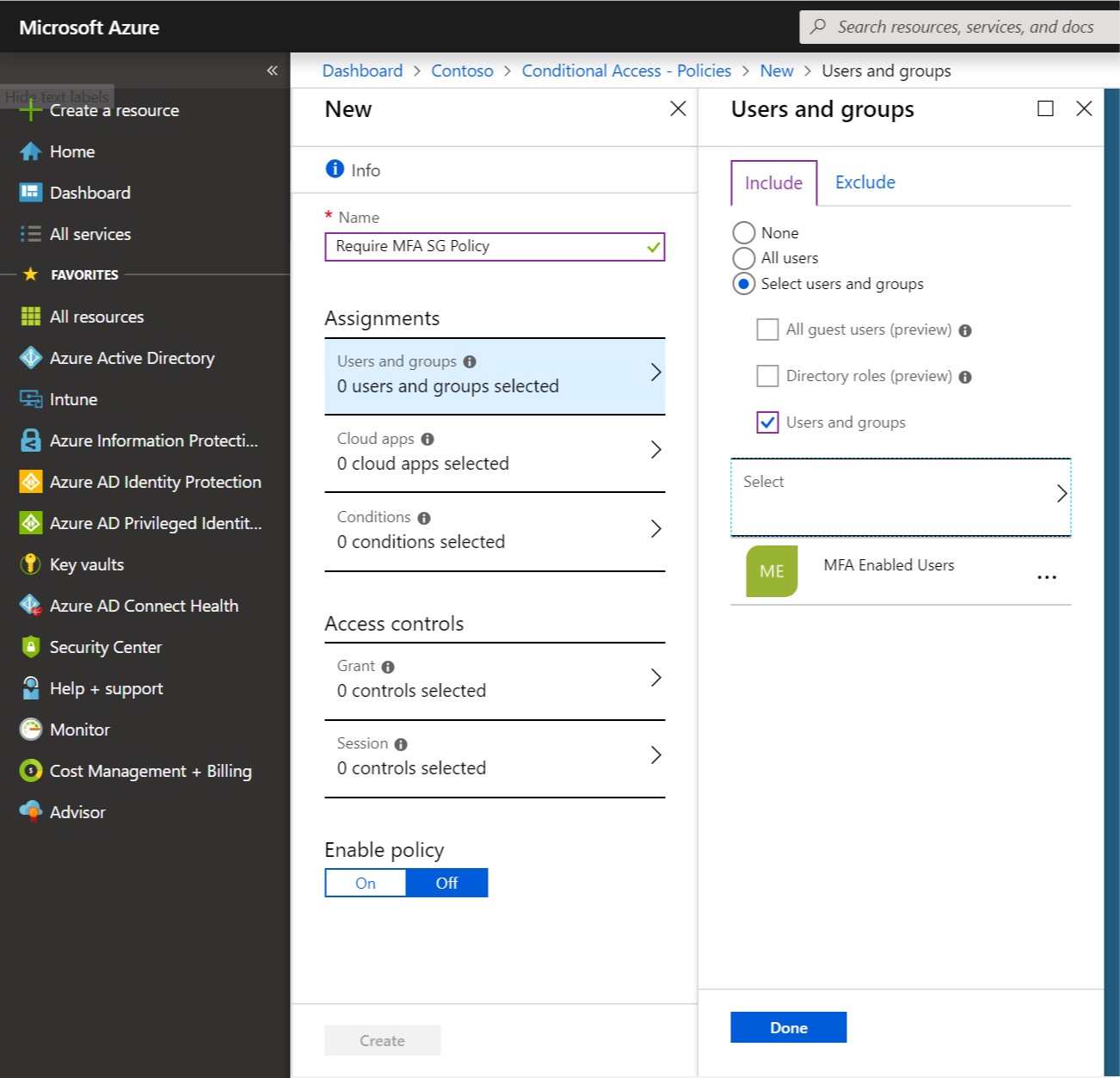
Next, have the Conditional Access Admin create a new Conditional Access rule with Assignments target set to the group created by the Helpdesk user.
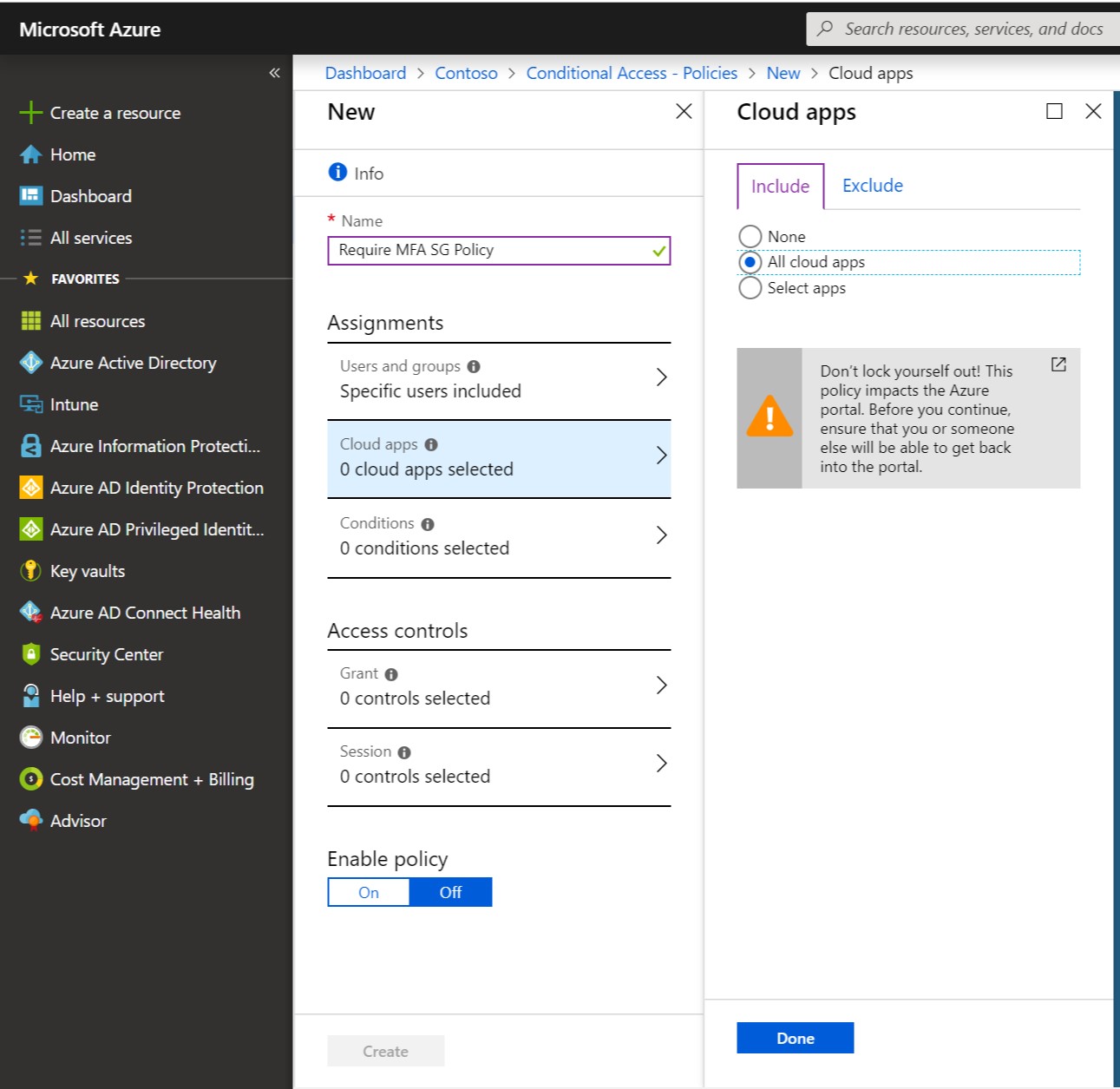
Next, select the Cloud apps you want to require MFA before allowing access, or select All Cloud Apps.
Next, choose the option to Grant Access and check Require multi-factor authentication.
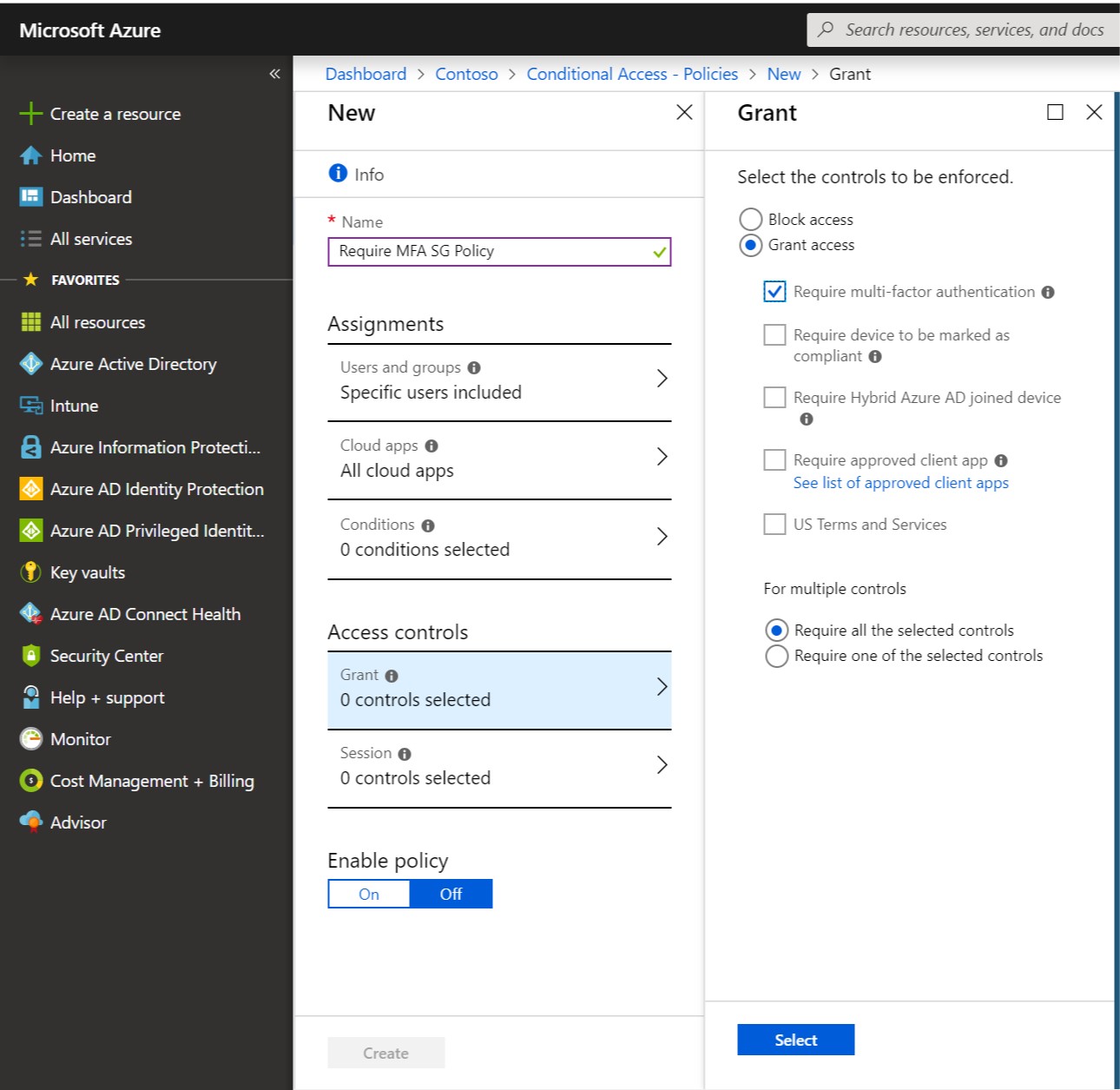
Finally, Enable the policy and choose Create.
Operations
Now, when the Helpdesk (someone with User Administrator Role) needs to enable or disable MFA for a user all they need to do is add (Enable MFA) or remove (Disable MFA) the user from your MFA Security Group.