I’ve seen a lot of asks from customer about how they can use Azure AD Groups with MDE Device Groups. Unfortunately, there isn’t a direct way to use Azure AD groups with the MDE Device groups, but there is an approach that provides a similar capability.
This approach is primarily works really well with client OS (Windows 10/11, etc.) and the scenario I’ll outline assumes:
- Devices are managed with Intune
- Devices are or will be onboarded to MDE
This solution can be utilize with other device management tools, but because we are trying to associate AAD Device Groups with MDE Device Groups then Intune is the most likely management tool.
MDE Registry Keys for Device Tags
MDE - Create and manage device tags
MDE has multiple ways you can create and manage device tags. One method is to set a registry key, so that once the device onboards, or syncs with MDE, the portal will ‘receive’ the machine tags from an onboarded device.
Intune
Since Intune is integrated with Azure AD it is able to leverage the Azure AD groups we are trying to bridge with MDE. Also, because Intune is the device management solution we can utilize it to push configurations to the device, like the registry keys, that MDE can then utlize. Thus Intune functions as a bridge technology for this scenario.
In the instructions below I have an AAD Device Group
US Devicesthat I will use to target the Configuration Policy. I will use the name of the AAD Device Group as the MDE Tag value so I can clearly map fromAAD Device Group => Device Tag. I will also use the same MDE Device Group name as the AAD Device Group and MDE Device Tag to make the obvious transition ofAAD Device Group => MDE Device Tag => MDE Device Group.
Windows 10/11 Configuration Policy
Create a Windows Device Configuration Profile in Endpoint Manager.
- In Endpoint Manager click on Devices, then under By platform click on Windows
- Choose Configuration profiles
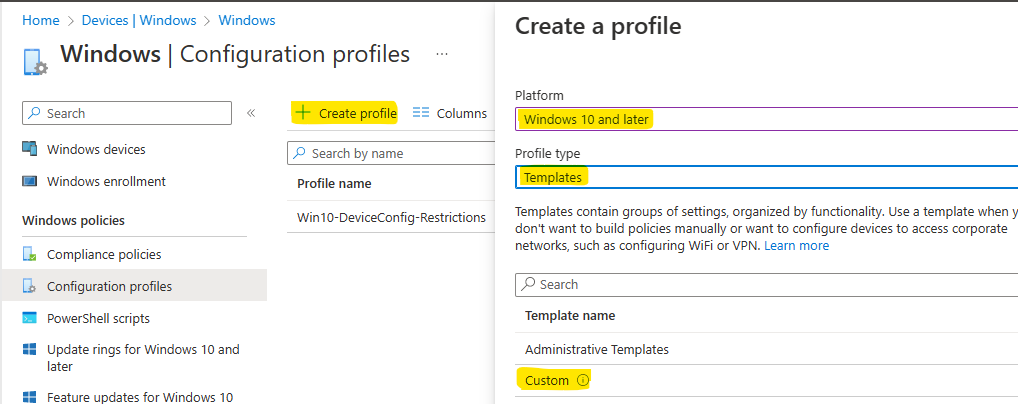
- Click + Create Profile and in the Fly Out select
- Platform: Windows 10 and later
- Profile type: Tempaltes
- Template name: Custom
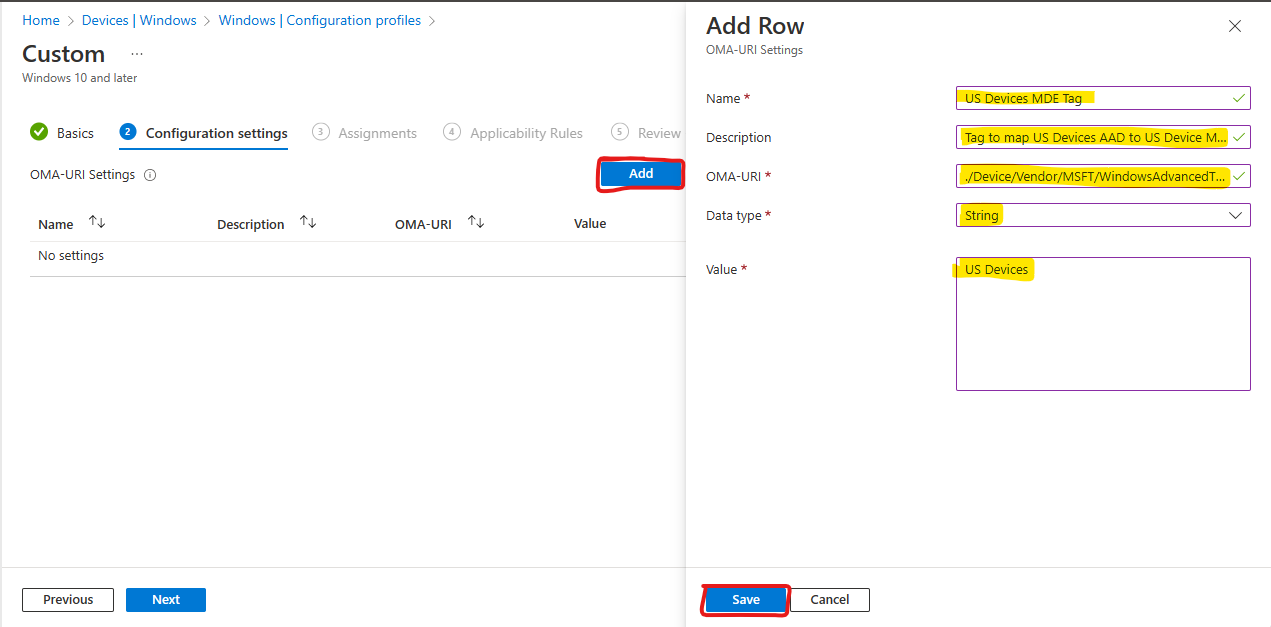
- Provide a name for your Configuration Profile like
US Devicesand click Next - Click Add to create an OMA-URI setting
- Provide a name like
US Devices MDE Tag - (Optional) Provide a description
- Input
./Device/Vendor/MSFT/WindowsAdvancedThreatProtection/DeviceTagging/Groupas the OMA-URI value - Select
Stringfor the Data Type - Input your desired tag value like
US Devices - Click Save
- Provide a name like
- Click Next
- Click Add Group to the Included Groups section and pick your device group then click Select
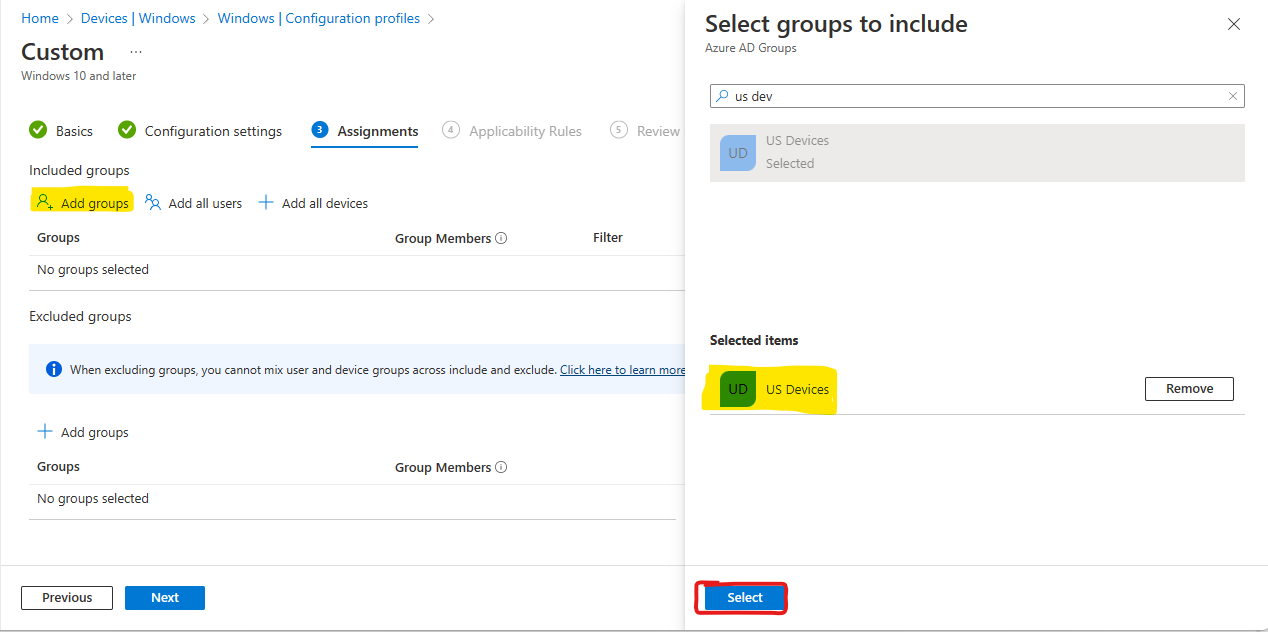
- Click Next and apply any Applicability Rules that are necessary, then click Next again
- Click Create
Now, any devices added to the AAD group you targeted will have the proper MDE Device Tag registry key pushed to them. Repeat these steps for other AAD groups you want to target.
Defender for Endpoint
Create a Device Group in Defender for Endpoint that will match the devices in the AAD Group by using the Device Tag
- In the Security Portal click on Settings and Endpoints
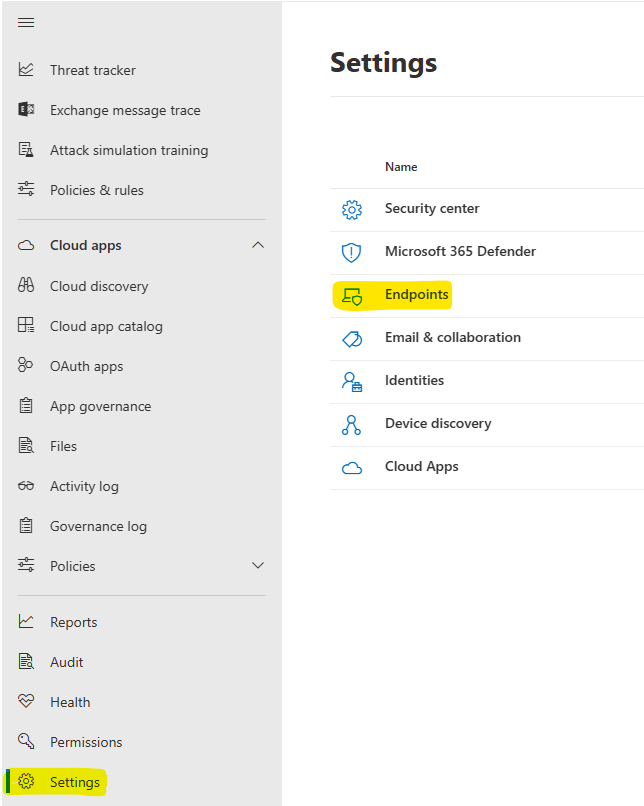
- Select Device Groups and then click + Add device group

- Provide a Device group name like
US Devicesand select the desired Remediation level and click Next - On the Devices condition for Tag select Equals for the condition and input the Device Tag value used in the above Intune section on Step 5.4 then click Next
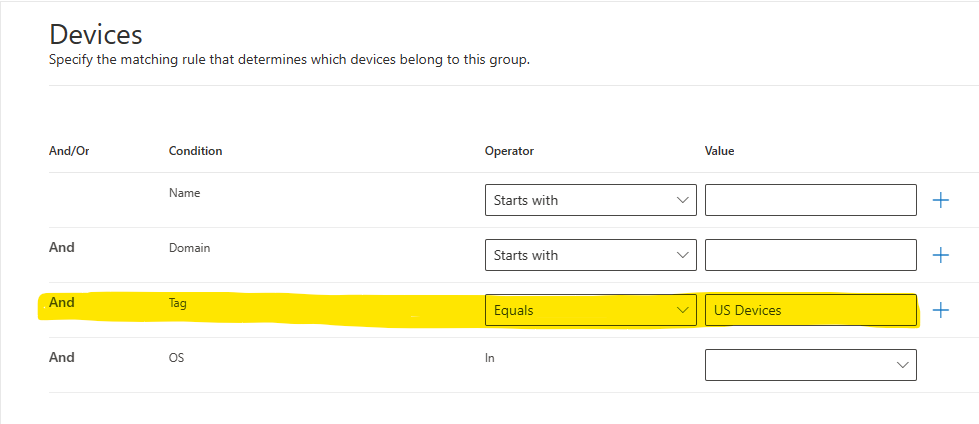
- On the Preview Devices you can view the machines, if the device tags have had time to propigate, that will be added to this Device Group, then click Next
- On the User Access page select the groups you wish to manage the devices if applicable, then click Submit
- Click Done
Now, any device with the Device Tag that matches you condition will be added to this Device Group. Repeat these steps for any other Device Group mappings you want to include.
Wrapping Up
With the instructions you can see how it is possible to replicate the device membership from an AAD group to an MDE Device Group eventhough it is not possible to directly map AAD Groups to MDE Device Groups. Be aware that there are propigation times realted to Intune pushing the Registry Key policy and a seperate propigation time for MDE Reading and Pushing the Device tag to the security portal.
Reference Documents
The following documents were used as references for creating this approach.
MDE - Create and manage device tags
Microsoft Defender for Endpoint Adding Tags for Multiple Devices from CSV List